Scams, ransomware, viruses…
Entering the Internet is exposing oneself to dangers that can end up infecting the device which is in use.
Every day, today can be considered a little battle, in reference to the statistics reports of the year which state that attacks on mobiles generate more money than those carried out on other devices (computers, servers, etc.), which is why hackers are always looking for new ways to infect terminals.
Cybercriminals take advantage of the low-security defense systems amid COVID-19 while almost everybody transitioned working from home. Enormous threats and vulnerabilities on mobiles have also been reported and were said to be the protagonists of the period.
With witnessed threats and attacks on global grounds, app developers and experts are asked questions upon the security of mobile app development android and are struggling to eliminate security issues in mobile phones.
The variety of protection methods are mushrooming which complicates the systematic risk assessment and guarantee of consistent and adequate security.
Various Types of Threats that Affect Mobile Apps Security
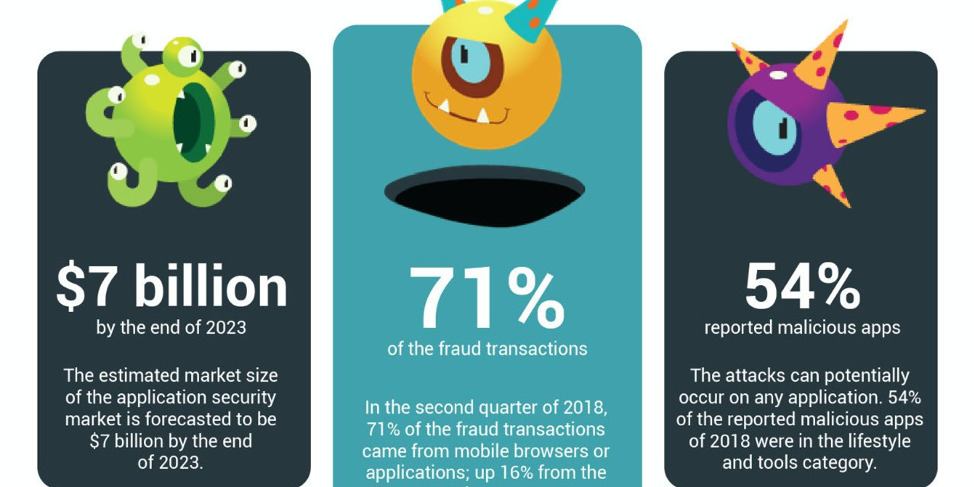
Mobile systems, the networks they connect to, and the applications they run can be exploited to steal confidential information in any form of the data. Cybercriminals can activate a mobile device’s microphone and camera to eavesdrop on closed-door meetings, and then can send recordings to a secret remote server.
Checkpoint has identified major categories of attacks and vulnerabilities that can challenge the security of a business and sensitive and crucial data of the users.
#System Vulnerabilities
Each version of a mobile device operating system has vulnerabilities that cybercriminals can exploit. The response to the correction of these vulnerabilities through updates or patches is notoriously late to the security needs of the market.
Critical security updates could take weeks or even months, leaving users exposed. Android is particularly vulnerable. The more than 24,000 different types of Android smartphones and tablets are not updated consistently so most devices continue to use older versions of Android where vulnerabilities have been found.
#Changes of Access to Root & Configurations Directories
Accessing the root directory of a smartphone or tablet (a practice also known as “Rooting” with Android or “Jailbreaking” with iOS) is no longer a hobby only for enthusiasts of gadgets. Root access allows for a wide range of customizations and settings. It also gives cybercriminals greater access, exposing devices and data to different risks.
#Re-packaged & Counterfeit Applications
Malicious applications can control mobile devices. The application may not be malicious, and users may not understand the permissions they grant the application during installation.
Even popular apps can be reverse-engineered into malicious code and distributed in an app store under a different name. Repackaged or renamed applications provide essential application functions but can also infect the user’s device.
#Man-in-the-Middle Attacks
Man-in-the-middle attacks can observe, intercept, and disrupt traffic between two devices. The risks of this attack are presented as copying credentials, spying on instant messages, or stealing confidential information. Alerts and warning signs on PCs and laptops are much more subtle and easily visible to the eye than those that can be detected on mobile devices.
#Ransomware
These programs access the mobile through the mentioned malicious app. They act by encrypting the files so that the user cannot access them and in return asks you to make a payment as a ransom.
#Adware
These are applications/software that secretly performs false clicks on advertising without the consent of the users, for attackers to attain benefit. This occurs, for example, a user is playing a game and covertly clicking on the screen is clicking on an advertisement.
#Keyloggers
These programs are camouflaged in apps and keep a record of the keys that are pressed on the device screen, thus, obtaining all kinds of information, such as, conversations or usernames and passwords for services accessed from the mobile.
#Trojans
These are apparently, legitimate and harmless apps, but on execution, gives offenders remote access to the infected mobile, i.e. they provide attackers with a backdoor to the device, thereby, allowing them to execute malicious code and infect it.
#Banking Trojans
They are a mixture of trojans and keyloggers and are presented through an app that looks similar to a bank but is not. With apps of such-kind, cybercriminals steal information related to your bank accounts.
#Advanced Persistent Threats (APT)
It is a type of attack that is characterized by combining in a sophisticated way several vulnerabilities and attacks at the same time to achieve its objectives.
For example, attackers use false profiles on social networks to deceive their victims through social engineering, chat with them and tell them to install fake messaging apps with which they infect the mobile with a trojan or ransomware.
They can also use the information obtained, through the permissions granted to the app, to extort money from the victim or sell it to third parties without the user’s knowledge.
[Prefer Reading: “Beware! Fake links promising to run banned Chinese App TikTok being circulated to steal user data.”]
The Continuation of Rise of Cyber Threats
Hackers and exploiters have tried and run many malware attacks and campaigns during the pandemic which were reported to be very intense in terms of threats and security flaws.
“Email is being the most used attack vector by cybercriminals during the pandemic.”
Cybercriminals have taken advantage of email distractions during the pandemic to spread their attacks. This is one of the most outstanding conclusions of the latest ESET barometer on security, which summarizes what happened in this area during the month of May.
Criminals continued their campaigns to spread banking trojans, taking advantage of the increasingly intense use made by users of online banking applications where many of them were targeted using themes related to COVID-19.
The offenders regularly used ‘overlay’ techniques to deceive users by impersonating banking apps to steal their access credentials. It was also discovered that a malicious Android application was created to trigger a denial of service (DDOs) attacks.
ESET’s website itself became the target of such attacks but fortunately, they were able to identify the app, analyze it, and report it to Google which quickly removed it from the Play Store.
Additionally, the Android operating system has also detected a crucial vulnerability to app security that allows malicious applications to pose as legitimate to steal sensitive information from users by requesting the entry of access credentials or other information.
[Prefer Reading: “How can AI better help Humans to Empower Cybersecurity?”]
Present Need: Deploy Vulnerability Management for Mobile Devices
Security professionals can no longer convince themselves that invisible vulnerabilities do not exist. The risk of mobile device threats is growing, and just as organizations use vulnerability management to protect their traditional endpoints from software vulnerabilities, they would do well to use it for their modern endpoints.
Vulnerability management tools for mobile devices can provide visibility into known vulnerabilities affecting iOS and Android devices, but tools that also provide risk assessment and action options will be more effective in ensuring continued risk reduction.
Some organizations see an increase in solution management with a mix of point solutions offering incremental and often rudimentary enhancements. These solutions can control the potential damage inflicted by lost or stolen devices, but only address the risks only on the surface.